Password is either being sent in plain-text, non-encrypted, or weakly hashed format.
What is the Vulnerability?
In a secure authentication system, user passwords should never be sent or stored in plain text. When a password is: Sent in plain text over the network (for example, via HTTP), Not encrypted during transmission, or stored with weak or outdated hashing methods (like MD5, SHA-1, or even Base64), it becomes very easy for attackers to intercept or crack it through brute-force methods.
Impact of the Vulnerability
Credential Theft:
Attackers monitoring network traffic (e.g., via MITM attacks) can capture user passwords.
Account Takeover:
Once credentials are stolen, attackers can log in as legitimate users.
Credential Stuffing:
Harvested credentials can be reused on other platforms if users reuse passwords.
Reputational Damage:
Customers lose trust in platforms that fail to protect sensitive information.
Regulatory Non-Compliance:
Violates data protection laws (GDPR, HIPAA, PCI-DSS, etc.).

Solution to Fix the Vulnerability
1. Enforce HTTPS (TLS 1.2/1.3)
Ensure all authentication endpoints use HTTPS.- Redirect HTTP to HTTPS
- Use HSTS headers
2. Never Store Passwords in Plain-Text
Passwords must never be stored in readable form in any system.3. Use a Strong Hashing Algorithm
Use adaptive, cryptographic password hashing functions such as:- bcrypt (preferred)
- scrypt
- Argon2 (winner of the Password Hashing Competition)
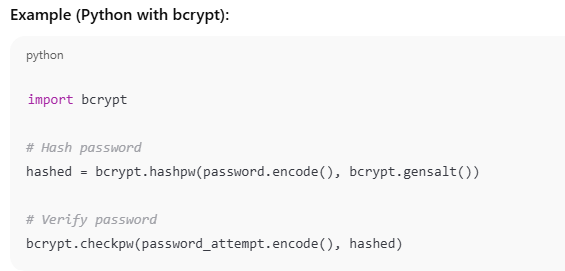
4. Use Salt + Pepper
- Salt: Unique per-user random value (automatically handled in bcrypt)
- Pepper: Global secret added to the password before hashing (store outside DB)

